
Meta is a medium difficulty rated linux box. It is retired now but I solved it when it was active. Even though it is labeled as medium difficulty, I found it pretty straightforward. It requires exploiting one ExifTool vulnerability to get into the system and using another CVE to get the user’s ssh private key. Privilege escalation is pretty simple.
Recon
Machine IP is 10.10.11.140. As always, first I ran Nmap,
nmap -sC -sV -oN nmap 10.10.11.140

It gave me results and it showed that we have two ports open, 22 for ssh and it says it is a Debian box. Port 80 for HTTP service was redirecting to http://artcorp.htb and indicated that it is running an Apache server.
I added artcorp.htb to my hosts config file.
Visiting the website (TCP port 80) is a simple static website. It is a simple apache page. At the bottom of the page, there are team members and their names which could be user names. Nothing else is interesting.

Ran gobuster to find directories, but the gobuster doesn’t seem to find anything interesting.
gobuster dir -u http://artcorp.htb -w ../wordlist/directory-list-2.3-medium.txt

At this point, I didn’t know what to do. So I thought of finding other subdomains which might lead to something. so I ran fuff to find subdomains and found one subdomain name- dev01
ffuf -w ../wordlists/SecLists/Discovery/subdomains-top1million-20000.txt -u http://artcorp.htb -H “Host: FUZZ.artcorp.htb" -mc 200

I added subdomain dev01.artcorp.htb to my hosts config file and visited the subdomain, and discovered a file upload point where we can upload images and get metadata.

so I tried to upload a reverse shell script to get a reverse shell but only images are accepted. so I thought to put a reverse shell script in the image to get a reverse shell, but I noticed the output of the application -

I immediately recognized the output style, it is similar to the ExifTool output style. That means the application is taking the uploaded image and runs ExifTool on that and returns the output.
since I didn’t know any ExifTool vulnerability, I searched on google and it returned a lot of results related to CVE-2021–22204.

Opened the GitHub link and read the README to understand how to use the exploit. It was pretty straightforward.
Foothold
Cloned the Github repo. In the exploit.py file, changed the IP with my local machine’s IP and PORT with the port I want to get a shell on.

Then ran exploit.py and it updated the image.jpg.

setup a netcat listener on the port 1337
nc -lnvp 1337
then uploaded the image.jpg and we got a reverse shell on our netcat listener-

User
we got the reverse shell, but can’t read the user flag. we have to log into the machine as user thomas -

ran pspy as www-data and noticed that a shell script called convert_images.sh running as a cronjob.

It seemed an interesting file, so looked at the script— it goes into /var/www/dev01.artcorp.htb/convert_images/ directory and runs mogrify to convert all files into png files.

since it uses mogrify, searched for any possible vulnerabilities. after a little bit of google search, I found a CVE on their official website.
The way to exploit this vulnerability is to upload an SVG to the /dev/shm directory of the machine and then copy it to /var/www/dev01.artcorp.htb/convert_images/. That SVG will have a command to copy thomas ‘s ssh private key and put it in a file in /dev/shm directory.

after some time, got the id_rsa -

download it to my local machine, and ssh-ed into the machine as user thomas
ssh -i id_rsa thomas@10.10.11.140

Root
First thing first, typed sudo -l command to check sudo permission of the user. I saw thomas user can run neofetch as root.

Also noticed that, $XDG_CONFIG_HOME was set. $XDG_CONFIG_HOMEdefines the base directory relative to which user-specific configuration files should be stored. So we can change the configuration file to escalate our privilege to root.
we can put our reverse shell script to config.conf which is in /home/thomas/.config/neofetch directory.

then exported thomas user’s .config to the base config env path.
export XDG_CONFIG_HOME="$HOME/.config"
Now, when neofetch gets executed as root, the root user’s config won’t be used but instead will be used thomas user’s config.
setup a netcat lister at 8080 port
nc -lnvp 8080
then run the neofetch as root
sudo /usr/bin/neofetch \"\"
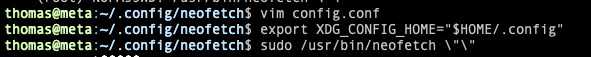
And, got a shell as root.

If you have any questions, you can ask them in the comment or you can DM me on Twitter.
I will be posting more write-ups for HackTheBox Linux boxes as soon as they retire. Until then, keep being awesome.
